The Hidden Dangers of Email Scams in Healthcare: A Guide for Practitioners

In the digital age, healthcare professionals like doctors, dentists, and veterinarians are not only tasked with caring for their patients but also with safeguarding their personal and practice information from the ever-present threat of cyber scams.
Email scams, in particular, have become a sophisticated tool for cybercriminals, often leading to disastrous consequences when successful. Understanding the risks and knowing how to recognize and respond to these threats is crucial for maintaining the integrity and security of your practice.
Recognizing the Bait: What Scammers Are After
Scammers targeting healthcare providers are often after one of two things: money or data. By sending a seemingly innocuous email with a request for service, like an inquiry about the cost of dental work accompanied by a link to “x-rays,” they bait providers into clicking on malicious links. These links can install spyware that can compromise your entire network, leading to data theft or ransomware attacks.
The data held by healthcare professionals is particularly valuable. It includes personal health information (PHI), financial details, and other sensitive data that, if exposed, can lead to identity theft and significant financial loss for patients. Furthermore, for the scammers, obtaining access to a healthcare provider’s email can be a goldmine, as it may contain correspondence with patients, insurance companies, and other healthcare providers.
The Perils of Clicking Unknown Links
Clicking on an unknown link can have several repercussions:
- Spyware Installation: As mentioned, this can give scammers access to your system and sensitive information.
- Ransomware: This type of malware can lock you out of your system and demand a ransom for access restoration.
- Phishing: Scammers might use the information to impersonate you or your practice, tricking patients or other providers into providing sensitive information.
- Network Compromise: The breach can spread across your network, affecting not just one computer but your entire practice.
HIPAA Compliance and Email Correspondence
Under the Health Insurance Portability and Accountability Act (HIPAA), healthcare providers are required to protect patient information from unauthorized access or disclosure. This means that any communication containing PHI should be conducted through secure, encrypted channels. Reminding patients never to send sensitive medical information through unsecured channels is also part of maintaining HIPAA compliance.
How to Spot Email Scams: Red Flags
Here are some tell-tale signs that an email may be part of a scam:
- Unsolicited Attachments or Links: If you receive an email with unexpected attachments or links, be wary.
- Urgency or Threats: Scammers often create a sense of urgency or use threatening language to prompt hasty actions.
- Mismatched URLs: Hover over any links without clicking to see if the URL matches what you would expect.
- Poor Grammar and Spelling: Professional communications should not contain multiple grammar or spelling errors.
- Requests for Sensitive Information: Legitimate organizations will not ask for sensitive information via email.
- Sender’s Email Address: Check if the email comes from a public domain or a misspelled official domain.
Real Client Example:
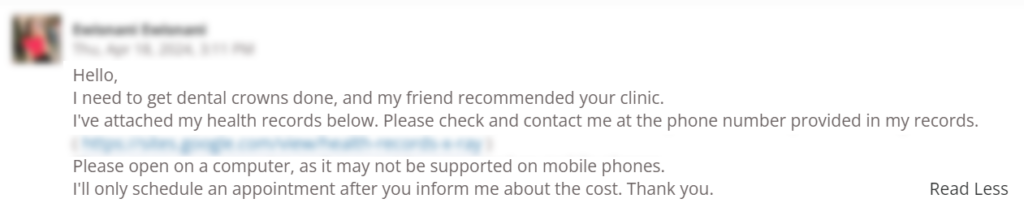
Best Practices for Email Security
To protect yourself and your practice from email scams:
- Educate Your Team: Make sure everyone in your practice knows how to recognize scam emails.
- Use Secure Communication Channels: Always use secure, encrypted methods for sending PHI.
- Implement Strong Password Policies: Use complex passwords and change them regularly.
- Keep Software Updated: Ensure all systems and antivirus software are up-to-date.
- Backup Data Regularly: Regular backups can help recover information in case of a ransomware attack.
- Verify Suspicious Requests: If an email request seems off, verify it through other communication means.
- Report and Delete Suspicious Emails: Report any scam attempts to appropriate authorities and delete the emails.
